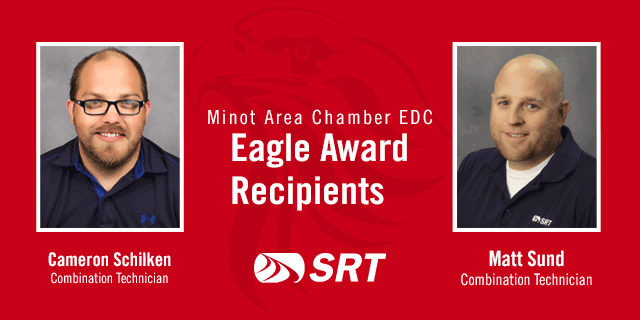
SRT Combination Technicians Cameron Schilken and Matt Sund received Minot Chamber EDC‘s Eagle Awards earlier this month. The Eagle Award recognizes excellence in customer service, and the recipients must be nominated to receive this award.
Matt and Cameron were nominated by an SRT customer who said, “Matt and Cameron hooked up our fiber optic cable. We have two big dogs and they had to be in their business while they were working and being a nuisance. Matt and Cameron took the time to acknowledge them. They were so professional and kind. They quickly hooked up our fiber optic and I had a question on my SRT email app. They not only took the time to help me but also took the time to look into the problem and not once made me feel like I was losing my mind. I hope SRT realizes what a gem they have. Thank you VERY much for your time and patience. We as a customer are very lucky to have you.”
Congratulations Matt and Cameron, and thank you for taking great care of our customers!



 Child identity theft happens when someone takes a child’s personal information and uses it to commit fraud. They could apply for government benefits, open a bank or credit card account, apply for a loan, or sign up for a utility service.
Child identity theft happens when someone takes a child’s personal information and uses it to commit fraud. They could apply for government benefits, open a bank or credit card account, apply for a loan, or sign up for a utility service.